5G in IoT & Smart Cities
1. what is 5G Security & Privacy?

5G Security & Privacy refers to the measures and technologies used to protect 5G networks from cyber threats, unauthorized access, and data breaches while ensuring user privacy. As 5G networks offer faster speeds, lower latency, and support for billions of connected devices, they also introduce new security challenges due to their complexity and large-scale adoption. To address these concerns, 5G networks implement advanced security protocols such as end-to-end encryption, network slicing security, and mutual authentication to safeguard user data and prevent malicious activities.
One of the critical aspects of 5G security is network slicing, which allows the creation of virtual networks tailored to specific use cases (e.g., autonomous vehicles, healthcare, smart cities). Each slice operates independently, ensuring that a breach in one slice does not affect others. To maintain privacy, 5G uses advanced encryption techniques like 256-bit encryption and user anonymity to protect sensitive information during transmission. Additionally, mutual authentication ensures that both the device and the network verify each other's identities, reducing the risk of man-in-the-middle (MITM) attacks. 5G also enhances security through software-defined networking (SDN) and edge computing, allowing rapid response to emerging threats and improved data isolation at the edge of the network.
Another key component of 5G privacy is user data protection. With billions of IoT devices connected via 5G, safeguarding personal information is crucial. 5G adopts Zero Trust Architecture (ZTA), where no entity—whether inside or outside the network—is automatically trusted. This approach enforces continuous authentication and strict access controls to protect sensitive data. Furthermore, 5G complies with global privacy regulations like GDPR and CCPA, ensuring that user data is collected, processed, and stored securely. By integrating AI-driven threat detection, 5G networks can proactively identify and mitigate cyberattacks, ensuring a safer and more privacy-focused digital environment.
2.5G Network Vulnerabilities
5G Network Vulnerabilities
Despite the advanced security features of 5G networks, they are still vulnerable to various cyber threats due to their complex infrastructure, massive connectivity, and distributed nature. One major vulnerability lies in the expanded attack surface—with billions of devices connected to the 5G ecosystem, every device becomes a potential entry point for cyberattacks. This increased connectivity exposes IoT devices, smart vehicles, and critical infrastructures to threats such as device spoofing, man-in-the-middle (MITM) attacks, and data interception. Weak security in these devices can lead to large-scale Distributed Denial-of-Service (DDoS) attacks, disrupting network operations. Additionally, edge computing—where data is processed closer to the source—introduces new risks as these decentralized nodes may lack proper security controls.
Another significant concern is signaling vulnerabilities in 5G protocols. While 5G improves security over 4G with mutual authentication and advanced encryption, certain signaling protocols like Diameter and SS7 remain weak points. Attackers can exploit these to track user locations, intercept calls and messages, or perform session hijacking. Network slicing, a core 5G feature that enables virtual segmentation of the network, also presents unique vulnerabilities. If one slice is compromised, it could allow lateral movement across other slices, affecting critical applications like autonomous vehicles or healthcare systems. Furthermore, supply chain vulnerabilities pose a serious risk—5G networks rely on components from multiple vendors, and a compromised device or software update could introduce backdoors for persistent threats.
Privacy risks are also heightened in 5G networks due to the vast amount of personal and location data being transmitted. Attackers can use IMSI-catchers (Stingrays) to track user identities, and despite encryption improvements, metadata leakage remains a concern. Nation-state actors and cybercriminals could exploit these vulnerabilities to conduct espionage or data harvesting. To mitigate these risks, 5G networks must adopt a Zero Trust model, ensure end-to-end encryption, implement AI-driven threat detection, and enforce regular security audits across the supply chain and network infrastructure.
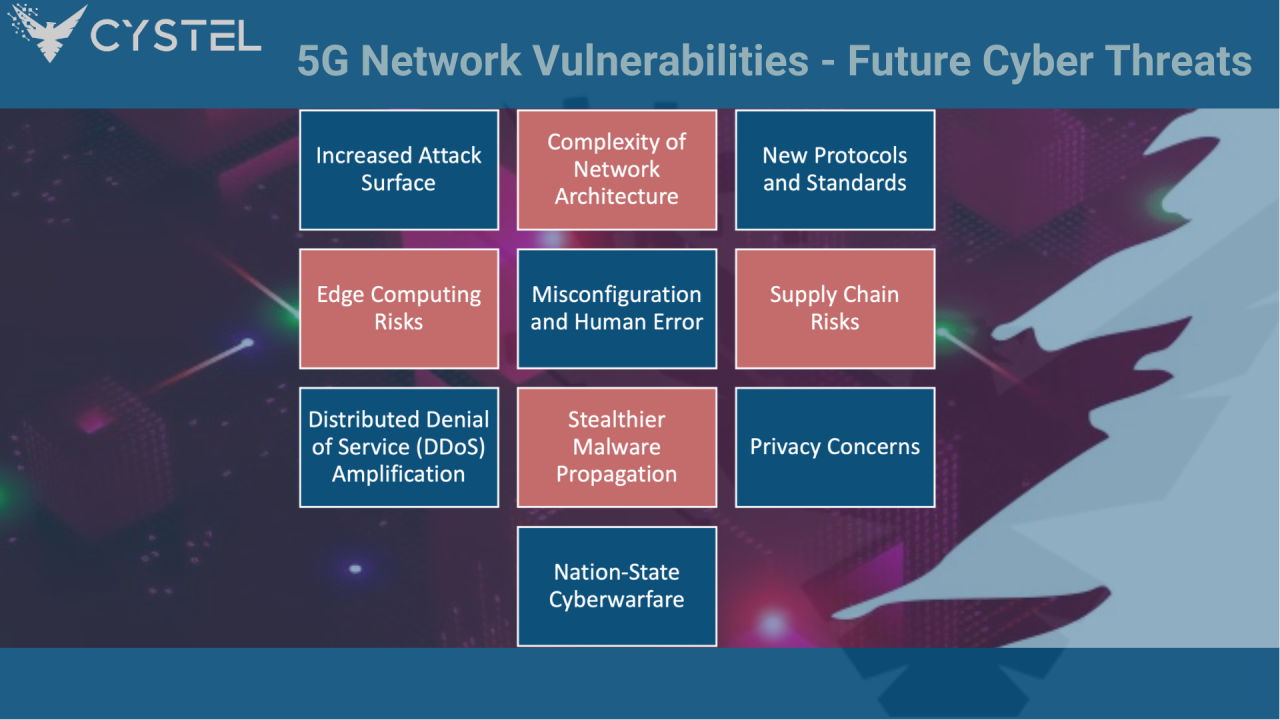
3.Threats to 5G Infrastructure
Threats to 5G Infrastructure
faces multiple threats due to its advanced architecture, increased device connectivity, and reliance on software-defined networks (SDN). One of the primary threats is cyberattacks on core networks. As 5G relies heavily on virtualized and cloud-based environments, it becomes vulnerable to Distributed Denial-of-Service (DDoS) attacks, data breaches, and man-in-the-middle (MITM) attacks. Hackers can exploit weak authentication or improperly secured APIs to gain access to critical infrastructure. Edge computing—where data is processed closer to devices—also expands the attack surface, making these decentralized nodes targets for malware and unauthorized access.
Another major threat is supply chain vulnerabilities. 5G infrastructure depends on hardware and software from multiple third-party vendors, increasing the risk of backdoors, malicious code, or faulty components being introduced. If an attacker compromises a vendor’s systems, they could infiltrate the entire 5G network. This poses serious risks for national security and critical services like emergency response systems and smart grids. Nation-state actors may exploit these vulnerabilities to perform espionage or disrupt essential services. Network slicing, a core 5G feature allowing virtualized segments for different applications, also presents a risk—if one slice is compromised, it may allow lateral movement across other slices, impacting critical sectors like healthcare and autonomous vehicles.
Physical infrastructure is also at risk. Small cell networks and base stations required for 5G’s high-speed connectivity are widely distributed and often located in public areas, making them vulnerable to tampering and physical attacks. Jamming and spoofing techniques can disrupt signal integrity, leading to service outages. Location tracking through vulnerabilities in the Signaling System 7 (SS7) or Diameter protocol can also compromise user privacy. To mitigate these threats, robust encryption, multi-factor authentication, and AI-driven threat detection must be integrated. Regular security audits and zero-trust architecture are crucial to maintaining the integrity of 5G infrastructure.
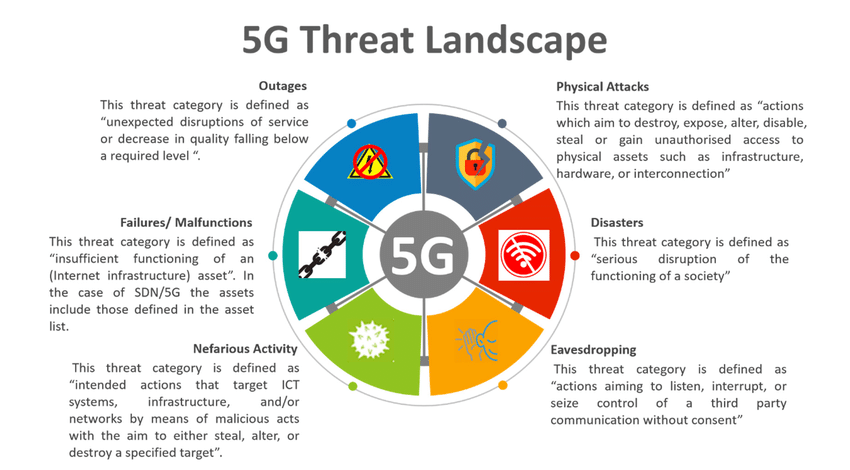
Threats to 5G Infrastructure
faces multiple threats due to its advanced architecture, increased device connectivity, and reliance on software-defined networks (SDN). One of the primary threats is cyberattacks on core networks. As 5G relies heavily on virtualized and cloud-based environments, it becomes vulnerable to Distributed Denial-of-Service (DDoS) attacks, data breaches, and man-in-the-middle (MITM) attacks. Hackers can exploit weak authentication or improperly secured APIs to gain access to critical infrastructure. Edge computing—where data is processed closer to devices—also expands the attack surface, making these decentralized nodes targets for malware and unauthorized access.
Another major threat is supply chain vulnerabilities. 5G infrastructure depends on hardware and software from multiple third-party vendors, increasing the risk of backdoors, malicious code, or faulty components being introduced. If an attacker compromises a vendor’s systems, they could infiltrate the entire 5G network. This poses serious risks for national security and critical services like emergency response systems and smart grids. Nation-state actors may exploit these vulnerabilities to perform espionage or disrupt essential services. Network slicing, a core 5G feature allowing virtualized segments for different applications, also presents a risk—if one slice is compromised, it may allow lateral movement across other slices, impacting critical sectors like healthcare and autonomous vehicles.
Physical infrastructure is also at risk. Small cell networks and base stations required for 5G’s high-speed connectivity are widely distributed and often located in public areas, making them vulnerable to tampering and physical attacks. Jamming and spoofing techniques can disrupt signal integrity, leading to service outages. Location tracking through vulnerabilities in the Signaling System 7 (SS7) or Diameter protocol can also compromise user privacy. To mitigate these threats, robust encryption, multi-factor authentication, and AI-driven threat detection must be integrated. Regular security audits and zero-trust architecture are crucial to maintaining the integrity of 5G infrastructure.
4.Encryption in 5G
Encryption in 5G
Encryption in 5G networks is a critical security measure that protects data confidentiality, integrity, and privacy as information is transmitted across the network. Unlike previous generations, 5G implements stronger encryption algorithms and enhanced security protocols to safeguard sensitive data from cyber threats. It uses 256-bit encryption for user data, which is a significant upgrade from 128-bit encryption in 4G. This advanced encryption standard (AES-256) ensures that even if data is intercepted, it cannot be deciphered without the appropriate encryption key. Additionally, end-to-end encryption (E2EE) is applied to protect communications between devices, edge servers, and the 5G core, ensuring user information remains private across all points in the network.
One of the core encryption mechanisms in 5G is User Plane Integrity Protection, which encrypts both user data (e.g., calls, texts, browsing) and signaling information (e.g., network commands and authentication requests). This encryption applies to both data in transit and data at rest, making it harder for attackers to perform man-in-the-middle (MITM) attacks. Another key feature is Subscription Permanent Identifier (SUPI) encryption, which replaces the traditional IMSI (International Mobile Subscriber Identity). This encryption prevents the tracking or eavesdropping of a user’s identity during communication, even when devices move between cell towers or switch from 5G to legacy networks like 4G or Wi-Fi.
5G also enhances mutual authentication using 5G-AKA (Authentication and Key Agreement) protocol. This method ensures that both the user device and the network verify each other's authenticity before data transmission begins. Encryption is also crucial for network slicing, where each virtual slice can have unique encryption keys to isolate and protect sensitive applications. This is particularly important for sectors like healthcare, finance, and autonomous vehicles, where data security is paramount. With these encryption technologies, 5G offers a multi-layered defense that reduces the risk of data breaches, eavesdropping, and identity theft, providing a more secure and private communication environment.

5.Role of AI in 5G Security
Role of AI in 5G Security
AI (Artificial Intelligence) plays a crucial role in enhancing 5G security by providing real-time monitoring, threat detection, and automated responses to cyberattacks. With 5G networks supporting billions of connected devices, the complexity and volume of potential vulnerabilities increase significantly. AI helps manage this complexity by analyzing large datasets from network traffic to identify anomalies and suspicious behavior that may indicate cyber threats. For instance, machine learning (ML) algorithms can recognize patterns and predict potential attacks, such as Distributed Denial-of-Service (DDoS) or phishing attempts, before they cause damage. AI also enhances encryption protocols by dynamically adapting security measures based on evolving threats, ensuring that user data remains protected across different devices and network slices.
One of the key AI applications in 5G security is behavioral analytics, which tracks user and device behavior to detect deviations from normal activity. For example, if a connected device suddenly transmits large amounts of data to an unknown destination, AI can flag this behavior as a potential data breach or malware infection. AI-powered systems also perform real-time threat intelligence, where they collect and analyze security data from multiple sources to identify new attack vectors. This proactive approach enables faster threat mitigation, reducing the impact of cyberattacks. Additionally, natural language processing (NLP) allows AI to scan text-based communications for signs of social engineering attacks, protecting both individual users and large organizations from targeted breaches.
AI also plays a significant role in automating security responses in 5G networks. Using Security Orchestration, Automation, and Response (SOAR) systems, AI can detect threats and automatically deploy countermeasures without human intervention. For instance, if a DDoS attack is detected, AI can reroute traffic, block malicious IPs, or isolate compromised devices to maintain network integrity. Furthermore, AI enhances Zero Trust Architecture (ZTA) by continuously verifying user identities and access permissions, ensuring only authorized devices and users interact with the network. As 5G continues to expand, AI-driven security systems will be essential to maintain data privacy, prevent cyberattacks, and provide secure and reliable connectivity for emerging technologies such as autonomous vehicles, IoT, and smart cities.

6.5G & Cyber Warfare
5G & Cyber Warfare
The rise of 5G technology has transformed cyber warfare by increasing the speed, connectivity, and potential attack surfaces for malicious actors. With faster data transmission and low latency, 5G networks support billions of devices, including smart cities, military communications, and critical infrastructure. This interconnected environment makes 5G networks a prime target for state-sponsored cyberattacks and espionage. Adversaries can exploit vulnerabilities in 5G systems to launch Distributed Denial-of-Service (DDoS) attacks, data interception, and infrastructure sabotage. For example, a cyber-attack on 5G-enabled power grids could cause widespread blackouts, while hacking autonomous vehicles could disrupt entire transportation networks. These advanced threats require robust cyber defenses to protect national security.
One significant risk in 5G cyber warfare is supply chain vulnerabilities. Many 5G components, such as base stations and network cores, are manufactured globally, raising concerns about backdoors and malware implants. Nation-states can exploit these weak points to conduct cyber-espionage, where sensitive information is stolen or manipulated. Additionally, network slicing—a core feature of 5G—creates multiple virtual networks within a single physical infrastructure. If attackers gain access to one slice, they could potentially breach other sections, leading to massive data leaks. Countries are now implementing strict regulations and working on secure supply chains to prevent adversarial nations from exploiting these technological weaknesses.
Artificial Intelligence (AI) also plays a dual role in 5G cyber warfare—both for offense and defense. Cyber armies use AI-powered algorithms to automate attacks, quickly finding vulnerabilities in 5G systems. For instance, AI-driven malware can adapt to changing network environments, making traditional defenses ineffective. On the defensive side, machine learning models help identify and mitigate threats in real-time. Additionally, 5G-enabled cyber warfare allows for advanced psychological operations (PsyOps) where misinformation and propaganda can spread rapidly across connected platforms. As 5G adoption continues to grow, governments and military organizations worldwide are investing in cyber resilience strategies to safeguard critical assets and maintain national security in an era where cyber warfare is as impactful as traditional armed conflicts.
7.Legal Regulations for 5G Security
Legal Regulations for 5G Security
Governments and regulatory bodies worldwide have introduced legal frameworks to ensure the security and integrity of 5G networks. These regulations focus on data protection, supply chain security, and network resilience to prevent cyberattacks and unauthorized access. In the United States, the Secure 5G and Beyond Act (2020) mandates the development of a comprehensive 5G security strategy. It emphasizes protecting national infrastructure, securing sensitive data, and reducing reliance on foreign manufacturers that pose security risks. Similarly, Europe’s 5G Toolbox provides a coordinated approach to risk assessment and mitigation, ensuring member states evaluate and secure critical 5G components against cyber threats.
In China, 5G networks are regulated under Cybersecurity Law and Data Security Law, which enforce data localization and strict surveillance practices. These regulations ensure that 5G-related data is stored and processed within national borders, reducing foreign access. India’s National Digital Communications Policy (2018) outlines security standards for 5G deployment, including supply chain verification and testing protocols to identify vulnerabilities. Countries like Australia and Japan also implement strict regulatory frameworks, banning high-risk vendors from participating in 5G infrastructure to maintain national security.
Global organizations like the International Telecommunication Union (ITU) and the 5G Infrastructure Public-Private Partnership (5G-PPP) promote international standards for 5G security. These guidelines focus on encryption protocols, network slicing security, and data privacy across cross-border 5G networks. Additionally, frameworks like the General Data Protection Regulation (GDPR) in Europe ensure that 5G networks comply with data privacy and user consent laws. Moving forward, legal frameworks will continue to evolve, addressing emerging threats such as 5G-based cyber warfare, supply chain risks, and AI-driven attacks to safeguard the future of global communications.

8.Future Challenges in 5G Security
Future Challenges in 5G SecurityThe evolution of 5G networks introduces advanced capabilities but also presents new security challenges. One significant concern is increased attack surfaces due to the massive number of connected devices. With the rise of Internet of Things (IoT) devices, each connection becomes a potential entry point for cybercriminals. These devices often have weak security and can be compromised, leading to large-scale attacks such as Distributed Denial-of-Service (DDoS). Additionally, network slicing—which allows different services to operate on isolated virtual networks—poses a challenge. If one slice is compromised, it could potentially affect other slices and disrupt critical services like healthcare and autonomous vehicles.
Another major challenge is securing data transmission across heterogeneous networks. As 5G relies on mmWave technology, which requires more base stations, there is an increased risk of interception and data breaches. Quantum computing also poses a future threat to 5G encryption methods, as it could break traditional encryption algorithms and compromise sensitive communications. Moreover, supply chain vulnerabilities remain a pressing issue. If malicious hardware or software is introduced during the manufacturing or distribution process, it could lead to backdoor access, allowing unauthorized surveillance or system manipulation.
Global regulatory compliance and cross-border coordination present additional challenges. Different countries implement varying security standards, making it difficult to maintain uniform protection. This lack of coordination can lead to inconsistent defenses against cyberattacks on international 5G infrastructure. Furthermore, the speed of 5G innovation may outpace the development of security frameworks, leaving gaps in protection. To address these challenges, future 5G security will require advanced AI-driven threat detection, post-quantum cryptography, and collaboration between governments, industries, and international bodies to create adaptive and comprehensive security measures.
Future Challenges in 5G SecurityThe evolution of 5G networks introduces advanced capabilities but also presents new security challenges. One significant concern is increased attack surfaces due to the massive number of connected devices. With the rise of Internet of Things (IoT) devices, each connection becomes a potential entry point for cybercriminals. These devices often have weak security and can be compromised, leading to large-scale attacks such as Distributed Denial-of-Service (DDoS). Additionally, network slicing—which allows different services to operate on isolated virtual networks—poses a challenge. If one slice is compromised, it could potentially affect other slices and disrupt critical services like healthcare and autonomous vehicles.
Another major challenge is securing data transmission across heterogeneous networks. As 5G relies on mmWave technology, which requires more base stations, there is an increased risk of interception and data breaches. Quantum computing also poses a future threat to 5G encryption methods, as it could break traditional encryption algorithms and compromise sensitive communications. Moreover, supply chain vulnerabilities remain a pressing issue. If malicious hardware or software is introduced during the manufacturing or distribution process, it could lead to backdoor access, allowing unauthorized surveillance or system manipulation.
Global regulatory compliance and cross-border coordination present additional challenges. Different countries implement varying security standards, making it difficult to maintain uniform protection. This lack of coordination can lead to inconsistent defenses against cyberattacks on international 5G infrastructure. Furthermore, the speed of 5G innovation may outpace the development of security frameworks, leaving gaps in protection. To address these challenges, future 5G security will require advanced AI-driven threat detection, post-quantum cryptography, and collaboration between governments, industries, and international bodies to create adaptive and comprehensive security measures.

Comments